Intel CScripts are very valuable for debug and validation of everything from smartphones to servers. They acquire even more power when they can be applied remotely.
One of the most powerful agents used in debugging low-level silicon, hardware, firmware and software issues on Intel platforms is In-Target Probe (ITP). ASSET of course has a core competency in this technology and delivers it on bench-top as well as embedded systems. The embedded, in-situ product is known as embedded ITP, and branded as ScanWorks Embedded Diagnostics (SED).
Intel provides a group of scripts to its customers that use ITP to provide validation, test and debug facilities when doing board bring-up or debugging firmware on hardware designs. These Intel Customer Scripts have classically been called “CScripts”. Their capabilities include basic state dump (register and memory), error injection, sideband-enabled post-mortem access, and many others. In their most common use case, the CScripts run on a host PC, which interfaces via an Ethernet or USB cable to an ITP hardware probe, which in turn connects via another cable to the board XDP header.
Situations where access to the board XDP interface, and therefore use of the CScripts at all, is difficult or even precluded are very common. Heat sinks and other board obstructions may block connection in the lab. Production systems may have the XDP headers physically removed to save cost. And in the field, getting access to the system via external hardware probes and cables is extremely problematic. Applications using SED eliminate these restrictions.
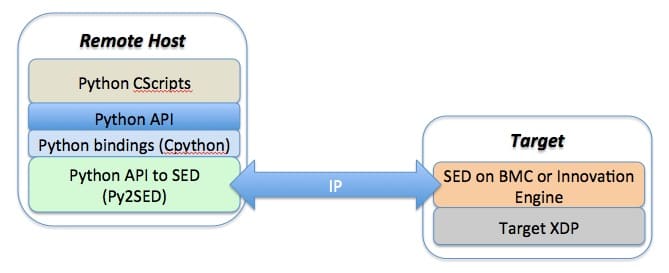
The topology of the SED-based remote application of CScripts is as follows:
Of course, the Python-based CScripts operate within a Python command environment, which allows for direct interaction with the target, as well as the creation of custom scripts by the user.
The power of this application is that the Remote Host and the Target can be in physically distinct geographies and time zones. Remote application of the CScripts can be performed over a secure IP network at an OEM’s ODM or contract manufacturer partner, and even at a customer’s field deployment location. This eliminates on-site visits as well as the need to plug a hardware probe into a target that may not allow physical access anyway. Cables, hardware probes, and even the occasional “duct tape” to strap the hardware probe to the side of the chassis are no longer needed.
Interested in learning more about ASSET’s implementations of CScripts or SED? Click on Intel Debug Using Python CScripts and ScanWorks Embedded Diagnostics Technical Overview.